AUTOSAR Adaptive: Cybersecurity included

The path to a smart connected vehicle leads via AUTOSAR Adaptive. To provide reliable protection against cyberattacks, this standard features security functions that can be integrated today into tomorrow’s E/E architectures.
AUTOSAR Adaptive provides the framework for new E/E architectures. In smart, highly automated vehicles, high-performance domain controllers (DCUs) and vehicle computers (VCs) and will take control. Against this backdrop, high data loads under real-time conditions call for powerful security mechanisms, which is why a range of security functions have been integrated into AUTOSAR Adaptive today.
Security modules in AUTOSAR Adaptive
- In AUTOSAR Adaptive, the targeted provision of cryptographic primitives, keys, and certificates is performed by the crypto stack (crypto API). Regardless of the crypto implementation, the applications access only the interfaces provided by the crypto stack, which increases the portability of applications to different ECUs.
- Secure communication is formed in AUTOSAR Adaptive with the help of TLS and IPSec. Both protocols enable the simple establishment of secure connections not only within the vehicle, but also with external instances such as the OEM backend. In addition, since the end of 2020, specifications have called for a protocol for SecOC (secure onboard communication) that is specific to AUTOSAR Adaptive.
- The AUTOSAR identity and access management module ensures that only authorized applications gain access to certain critical resources (e.g. sensitive data in the persistent memory, communications channels, cryptographic keys). These access rights can be configured in AUTOSAR Adaptive as required and updated at any time.

- An important component of effective security management throughout the vehicle life cycle is an intrusion detection system (IDS) that detects attacks on the vehicle and reports them to a backend. For this reason, the IDS manager (IdsM) is the latest feature to be integrated into AUTOSAR as a crucial control point for a distributed IDS.
- The secure update function in AUTOSAR Adaptive then helps fix any weaknesses identified by receiving and processing security updates for individual applications or even for the entire platform. The individual update blobs are signed by the backend, so that only updates from trustworthy sources are executed.
- ECU, DCU, and VC applications must also be verified at regular intervals. This task is conducted by either secure boot or the trusted platform function in AUTOSAR, which, as a trust anchor, verifies all applications as well as the platform itself. This ensures that only trusted software is executed.
RTA-VRTE: Platform software framework for AUTOSAR Adaptive
Future users of AUTOSAR Adaptive must familiarize themselves with the new architecture today. The ideal basis for integrating and implementing not just the security functions but also all other AUTOSAR Adaptive-compliant processes is the platform software framework known as real-time application vehicle runtime environment, or RTA-VRTE. RTA-VRTE contains all the important middleware elements for microprocessor-based vehicle computers. The platform software framework enables the function of virtual ECUs to be simulated on conventional desktop PCs and networked via Ethernet. RTA-VRTE creates a virtual machine consisting of four layers of basic software architecture, with the fifth layer then containing the vehicle-specific platform services.
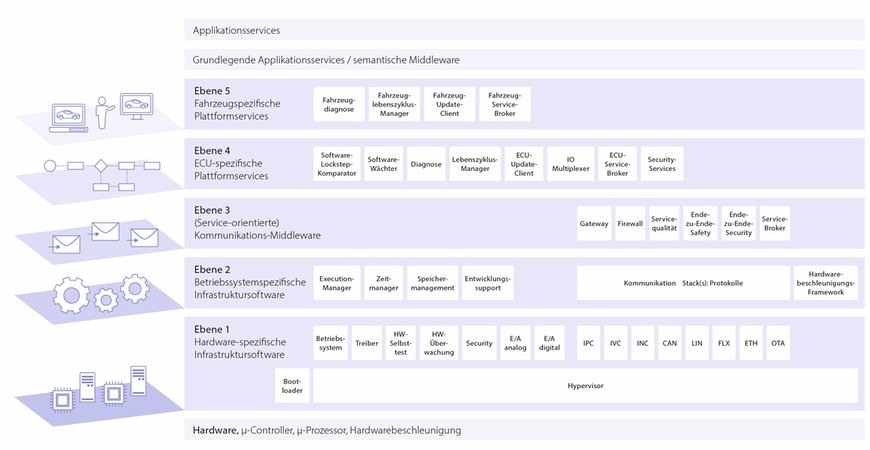
Levels 1 and 2 contain the infrastructure software for the hardware used (e.g. device drivers) and a POSIX-compliant operating system. Level 2 also provides platform-specific elements that derive from the AUTOSAR Adaptive specifications – an important one being execution management. This manages the dynamically assigned applications, ensures that they are started and stopped correctly, and monitors the assigned resource and execution limits. Execution management is thus a key function in IT security, providing the trusted platform and verifying the integrity and authenticity of Adaptive applications.
Early Access Program as start-up aid
In addition, the level 3 communication middleware ensures that the dynamic, flexible Adaptive applications and the other software applications can be integrated into the system. As a core component in RTA-VRTE, communication management controls the interaction between the levels and guarantees the smooth operation of the encapsulated software including the ECU- and vehicle-dependent platform services on levels 4 and 5. In securing end-to-end communication between services offered by authenticated applications, this function is also highly relevant to cybersecurity.
In 2020, RTA-VRTE began to be used around the world in projects aiming to bring AUTOSAR Adaptive vehicle platforms to production. In addition, ETAS and ESCRYPT offer an Early Access Program (EAP) that enables OEMs and suppliers to explore the development methodology of next-generation hybrid E/E architectures while anchoring the security components currently available through AUTOSAR Adaptive in their future vehicle architecture.
www.escrypt.com

