www.auto-innovations.net
17
'20
Written on Modified on
Escrypt News
Penetration testing: The acid test for cybersecurity
With increasing vehicle connectivity and automation, IT security functions have long since become an indispensable part of the in-vehicle network and its components.

But when it comes down to it, how safe are the ECU and vehicle network really from unauthorized access and manipulation? Penetration testing, or pentesting, is one of the most effective methods to answer this question. It involves the tester uncovering potential IT security gaps by attempting to penetrate the system – similar to the way a real attacker would.
In the automotive sector, pentesting is typically used to test individual ECUs, several ECUs in a network, or even complete vehicle platforms. It often starts at a late stage in the development process, when at least some of the functions essential for the test are complete. Unlike purely automated test procedures, pentesting includes an in-depth, customized examination of the system by a security expert under realistic conditions. The results are often decisive for the system’s marketability and approval for market launch in terms of IT security. And in some cases, penetration tests can also be useful and necessary even after the start of production – for example, if security gaps unexpectedly appear when the vehicle is in the field, key tests are missed, or new attack techniques become known.
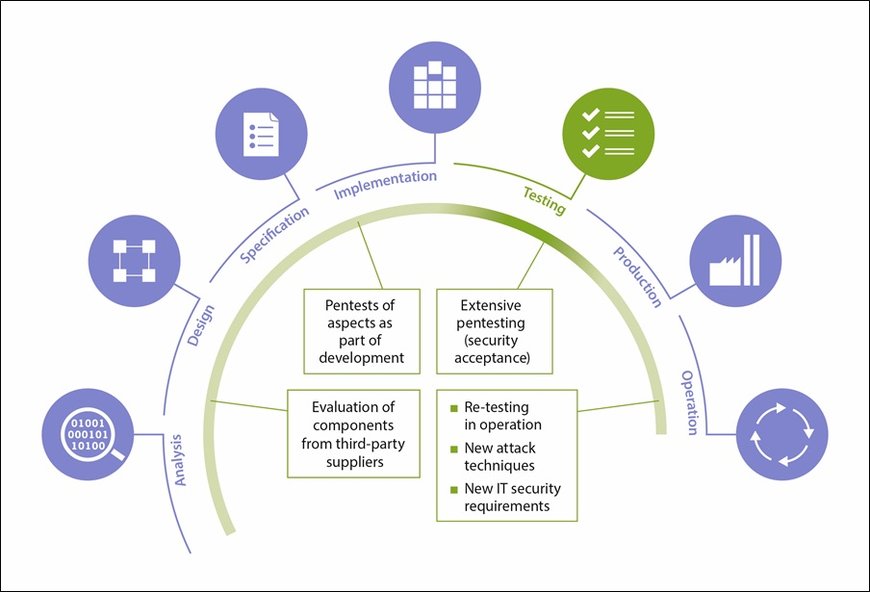
Penetration tests are often performed toward the end of the development process; in some cases, they are also useful in other phases of the product life cycle.
Comprehensive testing expertise required
As a rule, penetration testers start off by using automated testing tools – ideally ones that can be adapted to the specifications of certain vehicle platforms or even individual ECUs. These automated tools quickly find known weaknesses in widely used services and protocols. However, this serves only as a basis for the pentesters’ actual work, which involves analyzing in depth the anomalies that the testing tool reveals. They do this by scrutinizing every last detail of the underlying data, data traffic, processes, and source code. They also consult other experts, search databases for attacks on similar targets, and piece together several errors that may appear harmless on their own but, when combined, create complex and potentially dangerous chains of attack. Manual pentesting by a security expert is the only way to gain a comprehensive understanding of the IT security that the test system offers in the event of an elaborate cyberattack.
White box: The more information, the more efficient the test
Accordingly, the pentesting team draws on all the available techniques and test methods, conducts fuzz tests, vulnerability scans, and side-channel analyses, and carries out code audits as well as tests of the physical system and its security functions. The more that a pentester knows about the system, the better equipped they are to effectively test its level of cybersecurity, identify weak points, and make suggestions for improvement. For that reason, penetration tests should ideally be carried out as white-box tests, which means the customer should provide as much information as possible: source code, residual bus simulation, complete documentation, development and diagnostic tools, access to the backend, etc. With black-box or grey-box testing, however, this information is available only in part or not at all. For that reason, these methods are used only if the tester is not authorized to access the information, for example for legal reasons, or if the source code of third-party suppliers is not available.
Iterative approach
Penetration testing always takes an iterative approach: identify potential points of attack and locate and probe existing weaknesses. The testing team then presents the existing security gaps and associated risks to the customer, and advises them on effective countermeasures. Accordingly, a detailed test report is provided at the end of each penetration test. This report lists the identified points of attack, applied test procedures, and all findings in detail. It also highlights possible solutions. In turn, this enables the identified IT security gaps to be closed, and retests confirm that either the system is sufficiently protected or that further security measures are required.
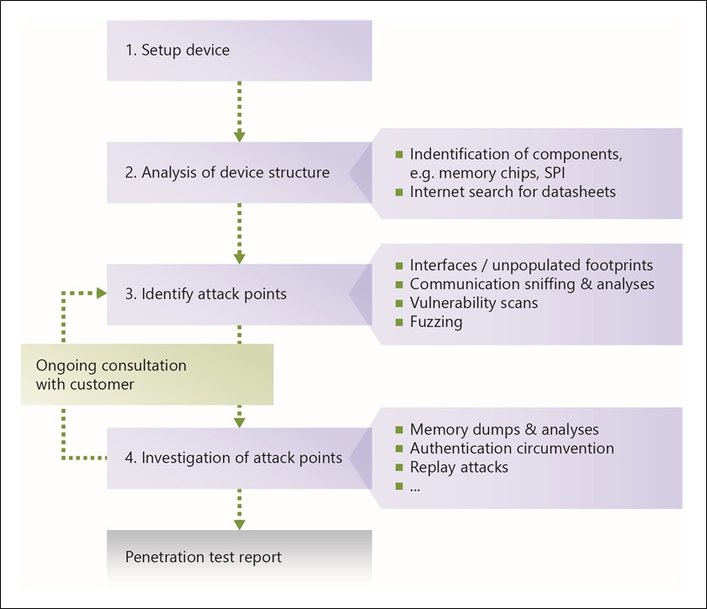
Sequence of automotive pentesting operations.
The highly sophisticated discipline of pentesting
With the new UNECE WP.29 regulations and the forthcoming ISO/SAE 21434 standard, certified cybersecurity management will very soon become a prerequisite for type approval. A security test strategy that fully penetrates the vehicle platforms, includes the supply chain, and addresses the vehicle life cycle is crucial. This is where the highly sophisticated discipline of pentesting comes in as the acid test for cybersecurity: by encompassing the test system both in detail and as a whole, pentesting uncovers IT security gaps before an attacker has the chance.
www.escrypt.com

